Welcome to the Ethical Hacker Course
i started ripping this course on August 30th of 2023
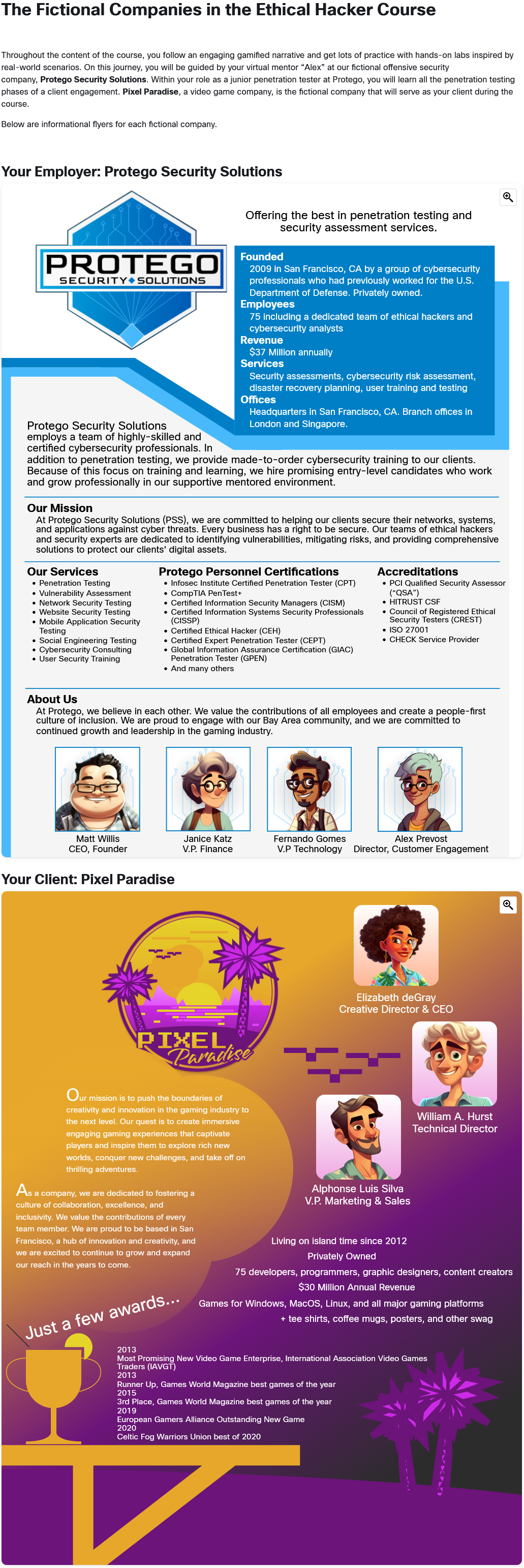
The Fictional Companies in the Ethical Hacker Course
Throughout the content of the course, you follow an engaging gamified narrative and get lots of practice with hands-on labs inspired by real-world scenarios. On this journey, you will be guided by your virtual mentor “Alex” at our fictional offensive security company, Protego Security Solutions. Within your role as a junior penetration tester at Protego, you will learn all the penetration testing phases of a client engagement. Pixel Paradise, a video game company, is the fictional company that will serve as your client during the course.
Below are informational flyers for each fictional company.
The digital landscape is evolving at an unprecedented rate and cyber threats lurk around every corner. Cybersecurity resilience in the modern world cannot be just an add on - it's a necessity.
Offensive security professionals like ethical hackers and penetration testers can help proactively discover unknown threats and address them before the cybercriminals do.
This course is designed to prepare you with an Ethical Hacker skillset and give you a solid understanding of offensive security. You will become proficient in the art of scoping, executing, and reporting on vulnerability assessments, while recommending mitigation strategies.
After completing this course, continue your cybersecurity career in offensive security (red team) as an ethical hacker or penetration tester. Or use this course to strengthen your defensive security (blue team) knowledge. By understanding the mindset of threat actors, you will be able to more effectively implement security controls and monitor, analyze, and respond to current security threats.
|
Module Title |
Module Objective |
|---|---|
|
Introduction to Ethical Hacking and Penetration Testing |
Explain the importance of methodological ethical hacking and penetration testing. |
|
Planning and Scoping a Penetration Testing Assessment |
Create penetration testing preliminary documents. |
|
Information Gathering and Vulnerability Scanning |
Perform information gathering and vulnerability scanning activities. |
|
Social Engineering Attacks |
Explain how social engineering attacks succeed. |
|
Exploiting Wired and Wireless Networks |
Explain how to exploit wired and wireless network vulnerabilities. |
|
Exploiting Application-Based Vulnerabilities |
Explain how to exploit application-based vulnerabilities. |
|
Cloud, Mobile, and IoT Security |
Explain how to exploit cloud, mobile, and IoT security vulnerabilities. |
|
Performing Post-Exploitation Techniques |
Explain how to perform post-exploitation activities. |
|
Reporting and Communication |
Create a penetration testing report. |
|
Tools and Code Analysis |
Classify pentesting tools by use case. |
In this course, you will explore and apply various tools and techniques within a controlled, "sandboxed" Ethical Hacker Kali Linux virtual machine environment to simulate cyber-attacks and discover, assess, and exploit built-in vulnerabilities. It is crucial to acknowledge that the hands-on labs are meant solely for educational purposes, aiming to equip you with the skills to identify and safeguard against real-world threats. The vulnerabilities and weaknesses demonstrated here must be used responsibly and ethically, exclusively within this designated "sandboxed" environment.
Engaging with these tools, techniques, or resources beyond the provided "sandboxed" virtual environment or outside your authorized scope may lead to violations of local laws and regulations. We strongly emphasize the importance of seeking clarification from your administrator or instructor before attempting any experimentation.
It is imperative to comprehend that unauthorized access to data, computer systems, and networks is illegal in numerous jurisdictions, regardless of intentions or motivations. We emphasize the significance of using your newfound knowledge responsibly and ensuring compliance with all applicable laws and regulations.
By accepting this "Ethical Hacker Statement," you acknowledge the critical importance of utilizing the skills acquired in this course for ethical and lawful purposes only, and you commit to upholding the principles of responsible cybersecurity practices. Remember, with great power comes great responsibility.
Your Acknowledgment
Do you acknowledge and accept your responsibility, as the user of this course, to be cognizant of and compliant with local laws, regulations, and ethical use?